Identifier: AIT-SA-20210215-02
Target: QCubed Framework
Vendor: QCubed
Version: all versions including 3.1.1
CVE: CVE-2020-24913
Accessibility: Remote
Severity: Critical
Author: Wolfgang Hotwagner (AIT Austrian Institute of Technology)
SUMMARY
VULNERABILITY DESCRIPTION
A SQL injection vulnerability in qcubed (all versions including 3.1.1) in profile.php via the strQuery parameter allows an unauthenticated attacker to access the database by injecting SQL code via a crafted POST request.
strQuery parameter of the serialized array in profile.php could lead to a SQL injection:
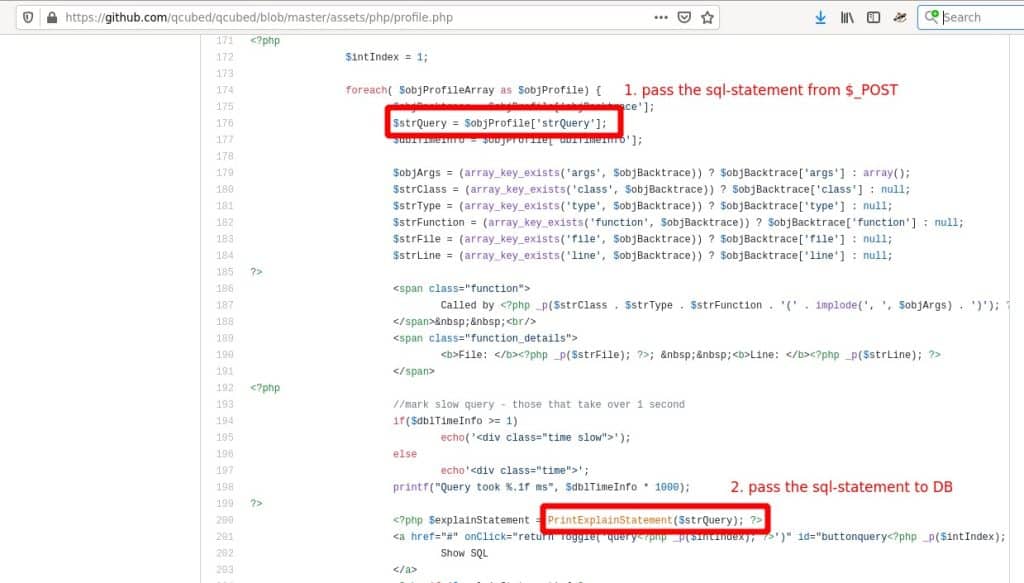
Inside the PrintExplainStatement()-function the query is passed to the ExplainStatement-method of the specific database-provider:
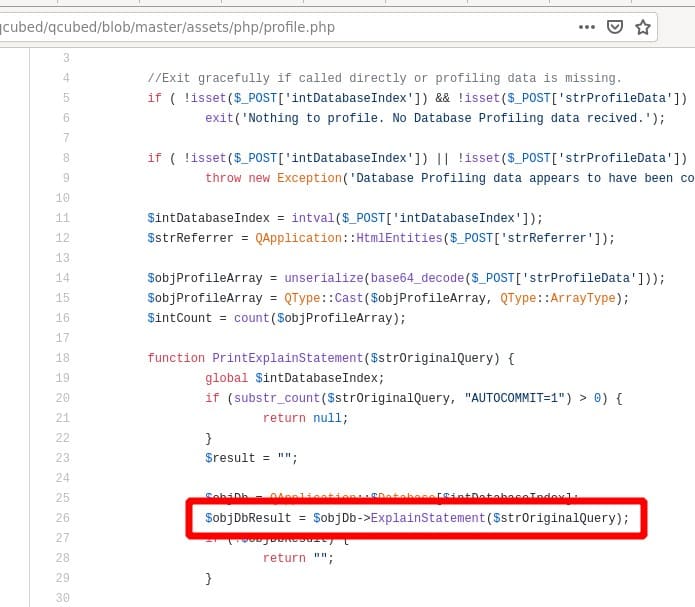
The ExplainStatement is a method of the specific database-provider. We tested the sql-injection with postgres and mysql(i). This could be exploited with both databases. Let’s see how it looks in the postgres-provider:
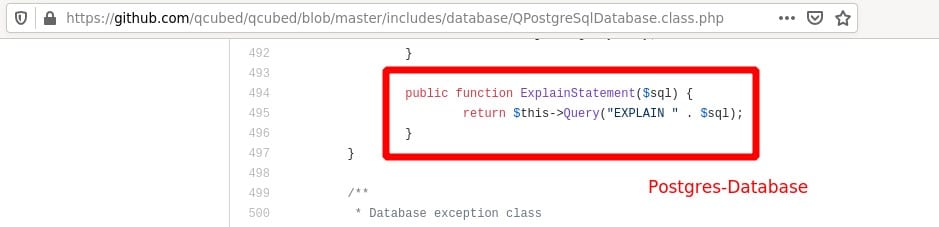
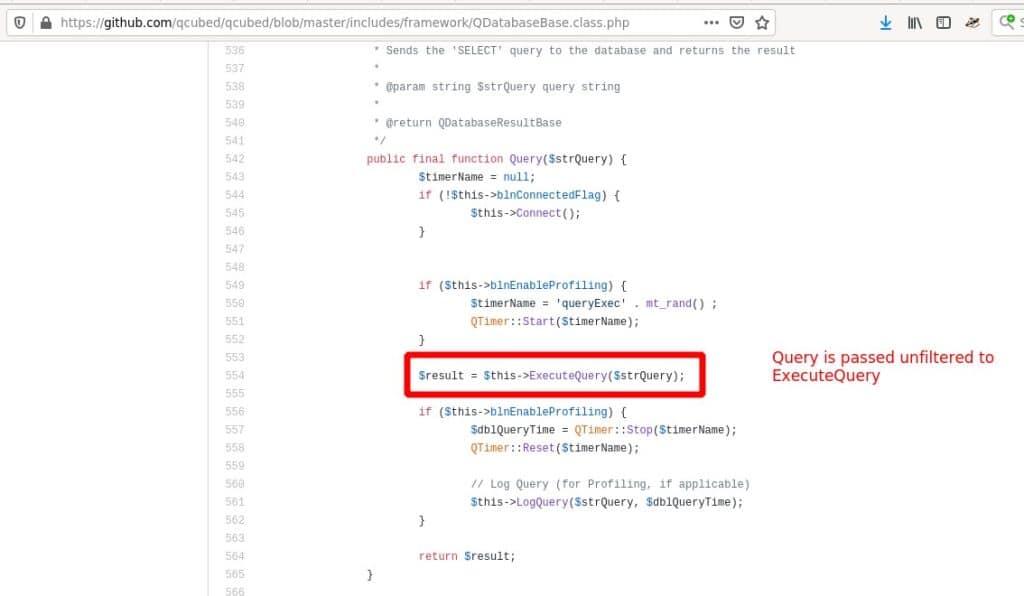
In ExecuteQuery it finally gets executed. Unfiltered:
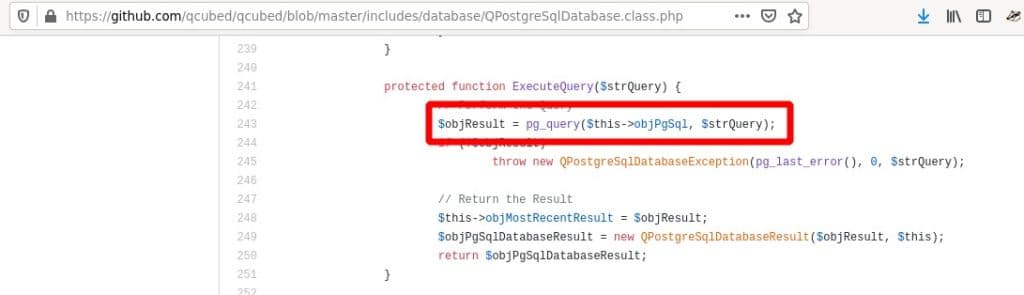
We were able to write proof-of concept exploit for mysql and postgres. Unfortunately with mysql we were not able to use a stacked-queries-payload and we had to exploit this vulnerability with a timebased approach.
VULNERABLE VERSIONS
All versions including 3.1.1 are affected.
TESTED VERSIONS
QCubed 3.1.1
IMPACT
An unauthenticated attacker could access the database remotely. In worst case scenarios an attacker might be able to execute code on the remote machine.
MITIGATION
VENDOR CONTACT TIMELINE
ADVISORY URL
WOLFGANG HOTWAGNER
Research Engineer /
Security & Communication Technologies