Identifier: AIT-SA-20240514-05
Target: FIWARE Keyrock
Vendor: FIWARE
Version: all versions including 8.4
CVE: CVE-2024-42167
Accessibility: Remote
Severity: Critical (9.1)
Author: Wolfgang Hotwagner (Austrian Institute of Technology)
SUMMARY
The function generate_app_certificates in controllers/saml2/saml2.js in all versions of FIWARE Keyrock including 8.4 does not neutralize special elements used in an OS Command properly. This allows an authenticated user with permissions to create applications to execute commands by creating an application with a malicious organisationname.
Proof of Concept
In file controllers/saml2/saml2.js there is a command execution that invokes openssl. By modifying the organisation name, it is possible to injection malicious commands. The following screenshot illustrates the organisationname that is simply concated to draft a command:
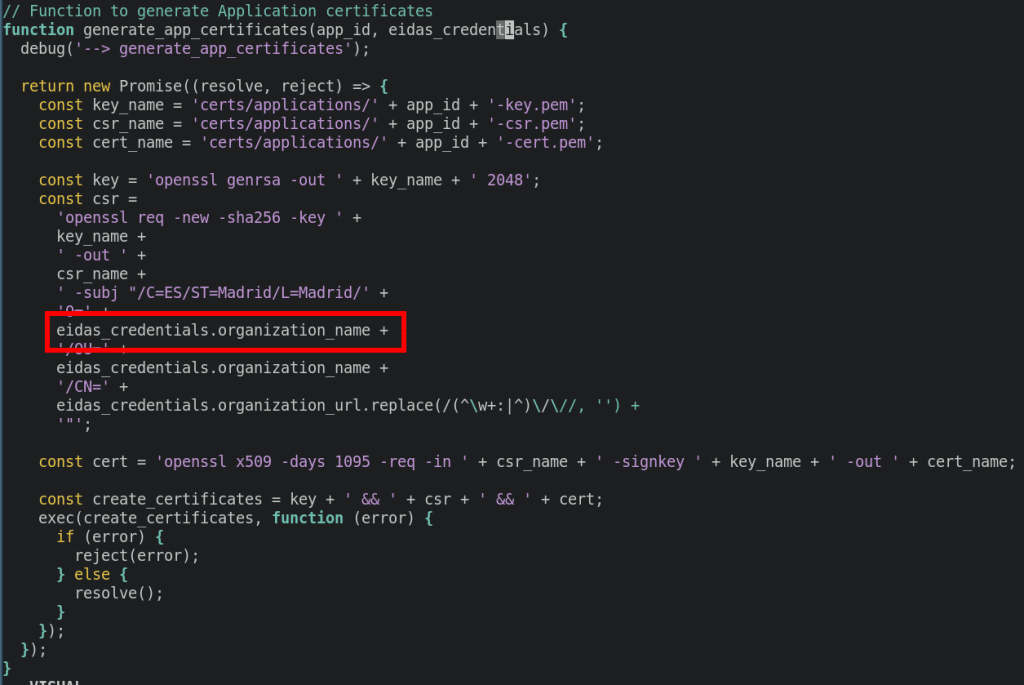
For further information see “Command Injection in Applicationname”
VULNERABLE VERSIONS
All versions including 8.4 are affected.
TESTED VERSIONS
FIWARE Keyrock 8.4
IMPACT
An authenticated user with permissions to create applications could inject shell commands by creating an application with a malicious organisationname.
MITIGATION
Currently (August 12th, 2024) there is no known mitigation.
VENDOR CONTACT TIMELINE
WOLFGANG HOTWAGNER
Research Engineer /
Security & Communication Technologies